The Breached Password Protection feature blocks and removes over 4 billion unique compromised passwords
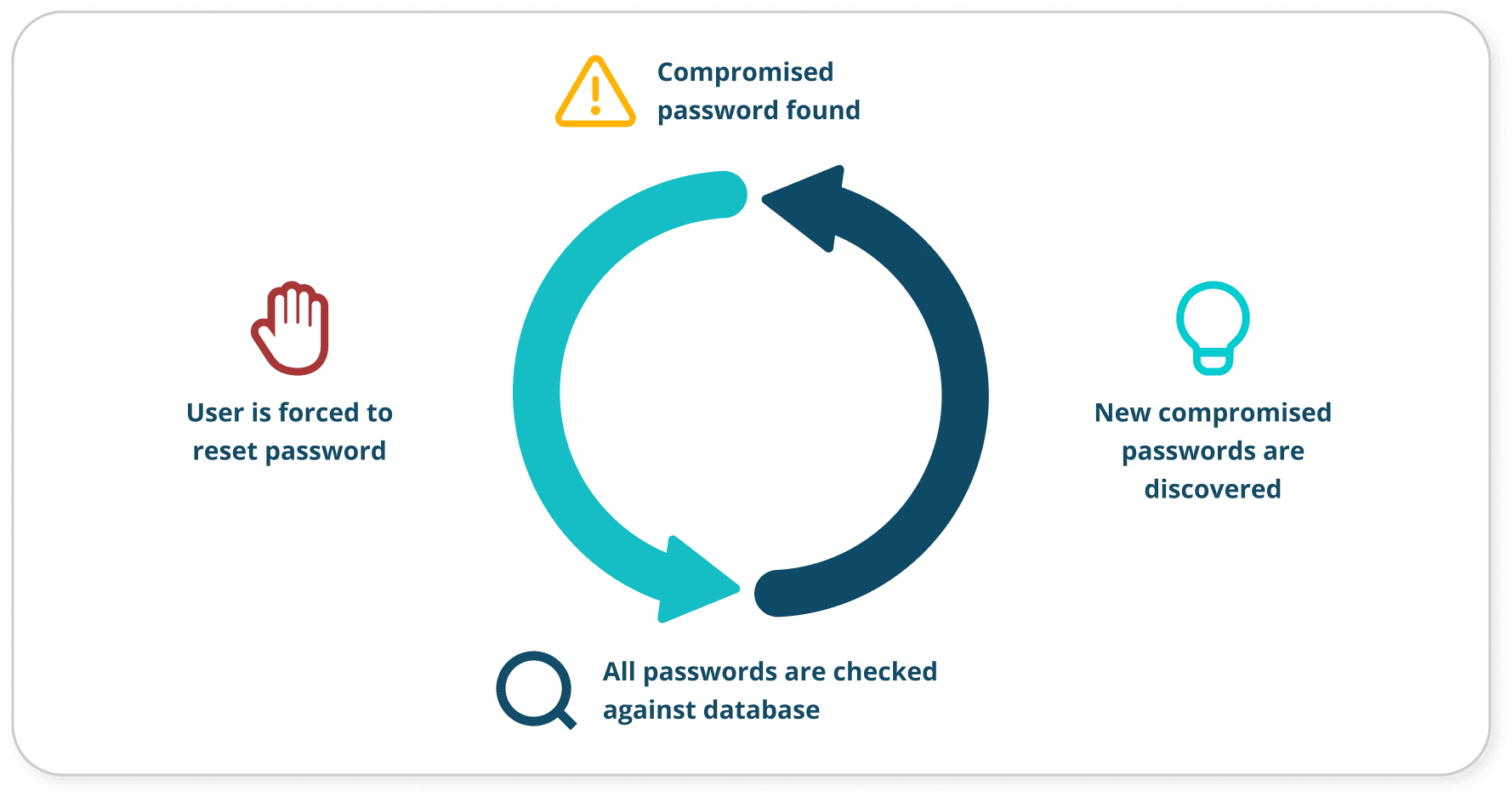
The continuous scanning feature identifies breached passwords daily, not just during password changes or resets
Includes passwords from real-time attack monitoring system, tracking live brute force attacks and malware-stolen data by our human-led Threat Intelligence team
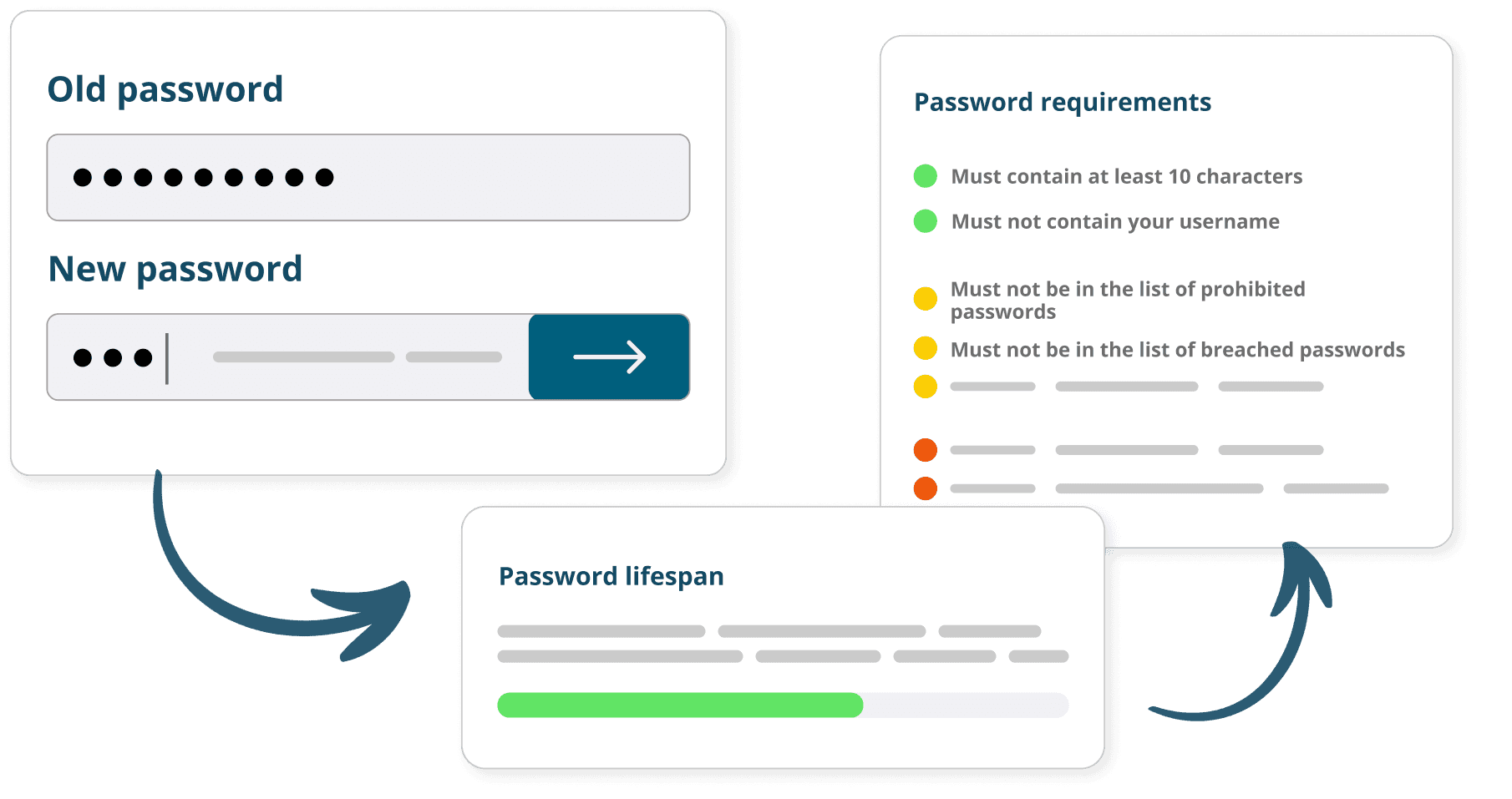
Dynamic feedback responds to user input, helping them create strong passwords they can easily remember
Customizable SMS and email notifications alert users if their password is compromised
A simple, easy-to-understand user experience prevents password frustration and fatigue, reducing calls and emails to the support desk
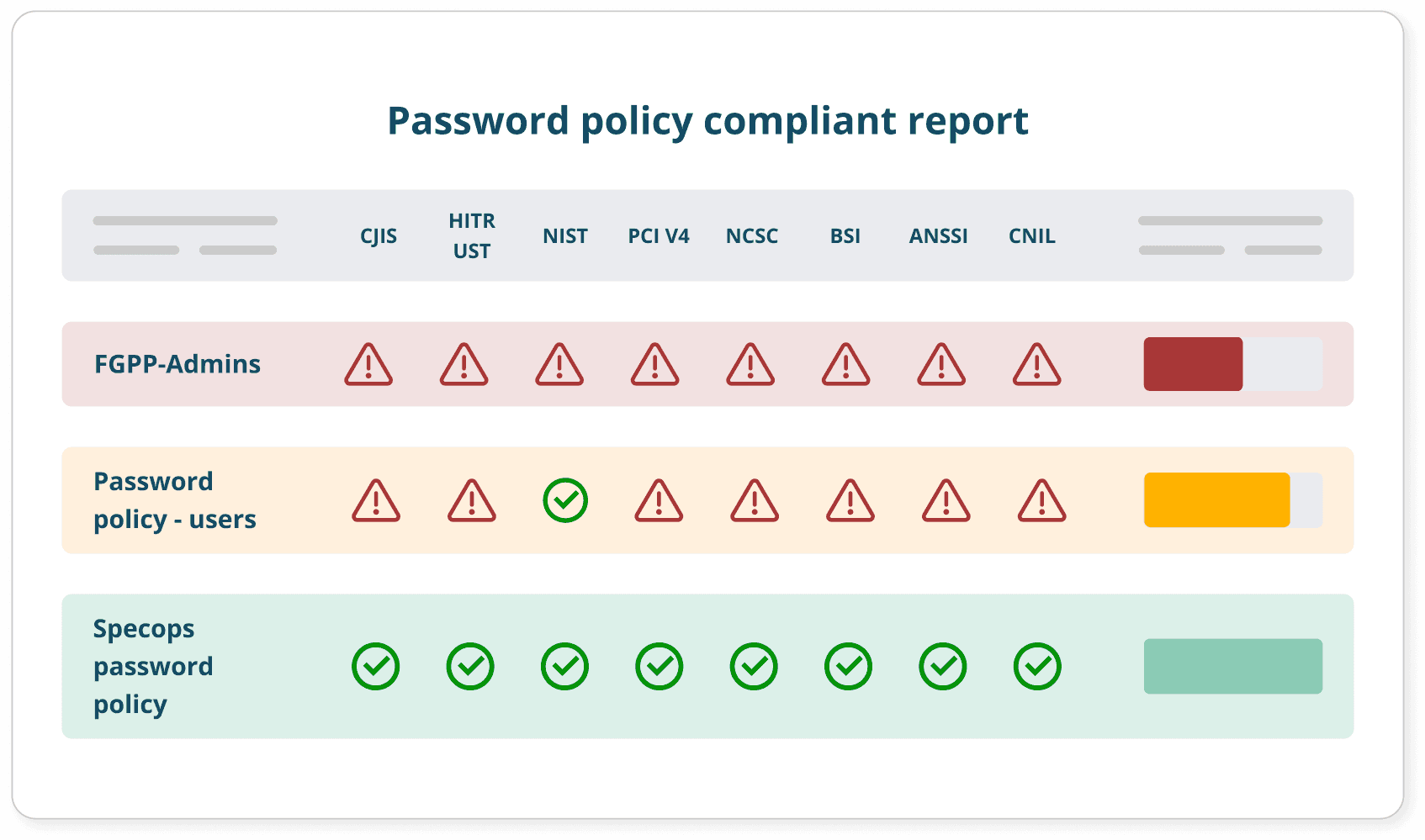
Ready-made compliance templates and reporting tool ensure you match standards
Comply with cybersecurity regulations (e.g. NIST, CJIS, NCSC, ANSSI,) and privacy regulations (e.g. CNIL, HITRUST, PCI)
"With this password manager, we never worry about password breaches or authorized access to applications and data. It makes creating strong passwords and managing those passwords easy and it is very secure too."
IT Services
“Our company needed a way to protect our staff from fishing impersonation calls as well as harden our password policy compliance so we could get our ISO 2700 certification. Specops provided all the tools we need all in one package.”
IT Security and Risk Management